secret of smart card Windows Security Smart Card popup. When starting my computer I get the popup attached below, it comes up and has to be dismissed a total of four times. This happens on two different Windows 10 devices I use. I use a smart card to access enterprise webmail on occasion and that works without issue. MOO. $128 to $376 for 400 cards. 514 templates in stock. Reprints or refunds if cards are defective. Thousands of 5-star ratings. "A+” rating from the BBB. MOO is an online print and design company that has been helping .
0 · Windows Security Smart Card popup
1 · Smart card
2 · Hackers can steal cryptographic keys by video
1. Write function does not require root phone. 2. The write function needs to buy a special white card. 3. After writing a white card, the white card becomes your access card, and .
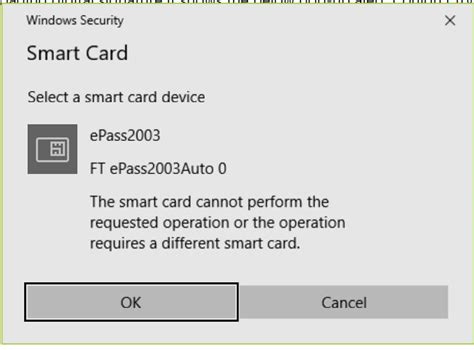
Researchers have devised a novel attack that recovers the secret encryption keys stored in smart cards and smartphones by using cameras in iPhones or commercial surveillance systems to video. Windows Security Smart Card popup. When starting my computer I get the popup attached below, it comes up and has to be dismissed a total of four times. This happens on two different Windows 10 devices I use. I use a . Researchers have devised a novel attack that recovers the secret encryption keys stored in smart cards and smartphones by using cameras in iPhones or commercial surveillance systems to video. Windows Security Smart Card popup. When starting my computer I get the popup attached below, it comes up and has to be dismissed a total of four times. This happens on two different Windows 10 devices I use. I use a smart card to access enterprise webmail on occasion and that works without issue.
How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.

A smart card (SC), chip card, or integrated circuit card (ICC or IC card), is a card used to control access to a resource. It is typically a plastic credit card-sized card with an embedded integrated circuit (IC) chip. [1] Many smart cards include a pattern of metal contacts to electrically connect to the internal chip.External security devices for this job typically take one of three forms: store secrets that PC computes on; do all secret storage and computation themselves; something in between. The cards that provide real security do the signing with onboard keys, preferably generated on .
Smart cards let you store the private key on a tamper resistant piece of hardware instead of scattered across various computers (where it can be accessed by other users of the machine, malicious software, etc). Smart cards make security better: They use secret codes to keep data private and stop wrong access. Smart cards are also handy and portable – you don’t need to remember hard passwords. Smart cards let you use extra checks too, like a code or your body, to make authentication even safer. Reply. AskMeForADadJoke • 31 min. ago. I believe the PIN is stored at the bank, so the cards chip has to match with the bank, and the PIN you type in yourself has to match with the bank, too. It's verifying both possession the device itself (the card/chip/account), and the human holder of it (the PIN) against the bank. 1. Reply.The first comprehensive discussion of power analysis attacks on smart cards. Examples and case studies illustrate the various attacks, from simple to differential power-analysis attacks. Detailed descriptions and comparisons of the effectiveness of different countermeasures.
Windows Security Smart Card popup
Smart-card messaging protocols cannot prevent a MITM attack between the card chip and the host computer without a pre-agreed secret (this is distinct from the card PIN and is actually used to protect message flow between card and host/computer) and there are many surreptitious ways to eavesdrop USB. Researchers have devised a novel attack that recovers the secret encryption keys stored in smart cards and smartphones by using cameras in iPhones or commercial surveillance systems to video. Windows Security Smart Card popup. When starting my computer I get the popup attached below, it comes up and has to be dismissed a total of four times. This happens on two different Windows 10 devices I use. I use a smart card to access enterprise webmail on occasion and that works without issue.
How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.A smart card (SC), chip card, or integrated circuit card (ICC or IC card), is a card used to control access to a resource. It is typically a plastic credit card-sized card with an embedded integrated circuit (IC) chip. [1] Many smart cards include a pattern of metal contacts to electrically connect to the internal chip.External security devices for this job typically take one of three forms: store secrets that PC computes on; do all secret storage and computation themselves; something in between. The cards that provide real security do the signing with onboard keys, preferably generated on . Smart cards let you store the private key on a tamper resistant piece of hardware instead of scattered across various computers (where it can be accessed by other users of the machine, malicious software, etc).
Smart cards make security better: They use secret codes to keep data private and stop wrong access. Smart cards are also handy and portable – you don’t need to remember hard passwords. Smart cards let you use extra checks too, like a code or your body, to make authentication even safer.
Reply. AskMeForADadJoke • 31 min. ago. I believe the PIN is stored at the bank, so the cards chip has to match with the bank, and the PIN you type in yourself has to match with the bank, too. It's verifying both possession the device itself (the card/chip/account), and the human holder of it (the PIN) against the bank. 1. Reply.
The first comprehensive discussion of power analysis attacks on smart cards. Examples and case studies illustrate the various attacks, from simple to differential power-analysis attacks. Detailed descriptions and comparisons of the effectiveness of different countermeasures.
switch lite nfc reader
nfc reader not working
Smart card
Hackers can steal cryptographic keys by video
Also, using amiibo cards is the only way to get design request from special characters. Do you .
secret of smart card|Smart card