access control card mapping The Card Format Tool Version 2 is a program that allows quick and visual aid in . To get complete information about working of nfc with LG G4 either you contact with LG Smart phone Experts or check Lg G4 Manual for help.
0 · access control system steps
1 · access control system design
2 · access control system
3 · access control software design
4 · access control software
5 · access control management system
6 · access control design guide
7 · access control design
13. First of all you have to get permission in AndroidManifest.xml file for NFC. The permissions are: The Activity which will perform NFC Read/write operation, add this intent filter .
access control system steps
In this guide, we’ll cover some of the best practices for managing access control .
The Card Format Tool Version 2 is a program that allows quick and visual aid in . The Card Format Tool Version 2 is a program that allows quick and visual aid in creating Card Formats for Access Control Manager (ACM). To download the tool at any time, visit: https://avigilon.app.box.com/s/pqm91jkge690otc28lliei8dqqtho2gm (note: this link will be inaccessible from our VPN as well as any other network/VPN that is restricted. In this guide, we’ll cover some of the best practices for managing access control systems, with a focus on integrating access levels, handling credentials, and optimizing hardware like fobs, maglocks, and request-to-exit devices. 1. Define and Segment Access Levels. One of the most fundamental elements of access control management is .
at home rfid chip
access control system design
Designing an access control solution requires decisions on 8 fundamental questions. This in-depth guide helps you understand the options and tradeoffs involved in designing an excellent access control solution. The eight fundamental questions are: Are the Benefits Worth the Cost? What Do You Secure? What Forms of Authentication and How Many .
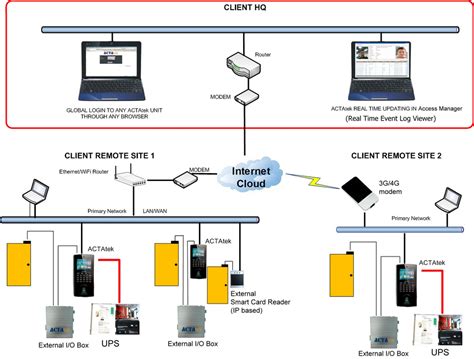
Traditionally, access control has been based on the identity of a user requesting execution of a capability to perform an operation (e.g., read) on an object (e.g., a file), either directly, or through predefined attribute types such as roles or groups assigned to that user.Use the access control examples and diagrams in this planning guide to design your access control system. Guarantee a solid security strategy from the start.Designing the architecture involves mapping out how different components interact. This includes the placement of readers and locks and how they connect to the central management system. Effective design ensures smooth operation and scalability for future expansion. Integration with Other Systems. Select the Right Type of Card. Many access control projects involve an upgrade to an existing system. An upgrade may integrate existing non-access control systems such as IP cameras that run over the network and are capable of reacting to an event initiated by a card swipe or proximity card.
Card access control systems are at the forefront of modern security solutions, offering a multi-layered defense against potential threats. Beyond traditional access control, these systems employ advanced features such as unauthorized access alerts, biometric integration, and real-time monitoring.
Throughout the course, students will explore a variety of topics related to access control card readers and access card format, including binary code and Wiegand formatting. Students will also learn about circuit diagrams, software integration, cloud-based access control systems, and more. Learn how access control card technology is evolving and the options you have for your business, so you can make the right decision. The Card Format Tool Version 2 is a program that allows quick and visual aid in creating Card Formats for Access Control Manager (ACM). To download the tool at any time, visit: https://avigilon.app.box.com/s/pqm91jkge690otc28lliei8dqqtho2gm (note: this link will be inaccessible from our VPN as well as any other network/VPN that is restricted.
In this guide, we’ll cover some of the best practices for managing access control systems, with a focus on integrating access levels, handling credentials, and optimizing hardware like fobs, maglocks, and request-to-exit devices. 1. Define and Segment Access Levels. One of the most fundamental elements of access control management is . Designing an access control solution requires decisions on 8 fundamental questions. This in-depth guide helps you understand the options and tradeoffs involved in designing an excellent access control solution. The eight fundamental questions are: Are the Benefits Worth the Cost? What Do You Secure? What Forms of Authentication and How Many .Traditionally, access control has been based on the identity of a user requesting execution of a capability to perform an operation (e.g., read) on an object (e.g., a file), either directly, or through predefined attribute types such as roles or groups assigned to that user.
rfid chip military
Use the access control examples and diagrams in this planning guide to design your access control system. Guarantee a solid security strategy from the start.
Designing the architecture involves mapping out how different components interact. This includes the placement of readers and locks and how they connect to the central management system. Effective design ensures smooth operation and scalability for future expansion. Integration with Other Systems.
Select the Right Type of Card. Many access control projects involve an upgrade to an existing system. An upgrade may integrate existing non-access control systems such as IP cameras that run over the network and are capable of reacting to an event initiated by a card swipe or proximity card.
Card access control systems are at the forefront of modern security solutions, offering a multi-layered defense against potential threats. Beyond traditional access control, these systems employ advanced features such as unauthorized access alerts, biometric integration, and real-time monitoring.Throughout the course, students will explore a variety of topics related to access control card readers and access card format, including binary code and Wiegand formatting. Students will also learn about circuit diagrams, software integration, cloud-based access control systems, and more.

access control system
3 - Now go to your file manager and search for a folder called ‘MifareClassicTool’ on the user root directory and you will see something like this. dump-files - The folder where you will add all .
access control card mapping|access control software