token or smart card authentication Certificate-based authentication is an encrypted method that enables devices and people to identify themselves to other devices and systems. Two common examples are a smart card or when an employee’s device sends a digital certificate to a network or server. Animal Crossing-themed Near Field Communication (NFC) capable amiibo trading cards that work with compatible games on the Nintendo Switch, Wii U and Nintendo 3DS family of systems. . Use an amiibo card in the Animal .Custom Animal Crossing Amiibo Cards. ALL Series are Available in our store. Fast Ship from United States. All orders will be shipped in 1 business day. 30 Days Money Back Guarantee. Sales Promotion up to 30% Off Discount. All Villagers are Available including Sasha, Shino, .
0 · what is smart card number
1 · what is smart card authentication
2 · smart card identity
3 · smart card identification
4 · smart card based identification system
5 · smart card based authentication
6 · memory based smart card
7 · azure smart card authentication
Saturday, January 9, 1988AFC: Cleveland Browns 38, Indianapolis Colts 21Felix Wright's interception deep inside his own territory sparked . See more
How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system. Some might involve a physical token containing the user's credentials, like a smart card or smartphone. Other methods might involve biometrics, using a specialized scanner or even a general-purpose device like a smartphone. In the digital world we live in, your choice of method of authentication is critical.
Token-based authentication is different from traditional password-based or server-based authentication techniques. Tokens offer a second layer of security, and administrators have detailed control over each action and transaction. The smart card checks the user’s name and password using secret codes and makes a digital signature or token. The token gets sent to the backend server to check. If it’s OK, the user can use the thing or system they wanted.Certificate-based authentication is an encrypted method that enables devices and people to identify themselves to other devices and systems. Two common examples are a smart card or when an employee’s device sends a digital certificate to a network or server.
A security token is a peripheral device used to gain access to an electronically restricted resource. The token is used in addition to, or in place of, a password. Discover the benefits, challenges, and best practices for implementation. Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and .
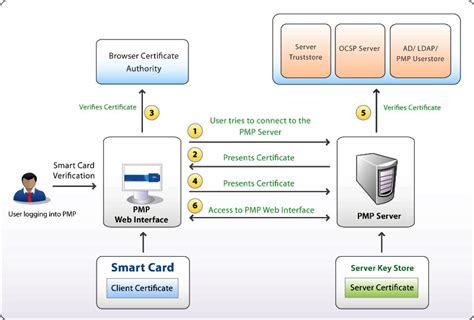
Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation.
Smart card authentication requires two things: the smart card itself and a pin entered by the user. With smart cards there are two different ways to authenticate yourself into a system, there is either contact or contactless smart card readers. A common instance of token-based authentication is a house key. Ideally, only the person who possesses the proper key can unlock the corresponding door. Similarly, there should only be one unique token per user. Besides physical keys, tokens can also be .How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.
Some might involve a physical token containing the user's credentials, like a smart card or smartphone. Other methods might involve biometrics, using a specialized scanner or even a general-purpose device like a smartphone. In the digital world we live in, your choice of method of authentication is critical.
Token-based authentication is different from traditional password-based or server-based authentication techniques. Tokens offer a second layer of security, and administrators have detailed control over each action and transaction. The smart card checks the user’s name and password using secret codes and makes a digital signature or token. The token gets sent to the backend server to check. If it’s OK, the user can use the thing or system they wanted.Certificate-based authentication is an encrypted method that enables devices and people to identify themselves to other devices and systems. Two common examples are a smart card or when an employee’s device sends a digital certificate to a network or server.A security token is a peripheral device used to gain access to an electronically restricted resource. The token is used in addition to, or in place of, a password.
Discover the benefits, challenges, and best practices for implementation. Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and .
Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation.Smart card authentication requires two things: the smart card itself and a pin entered by the user. With smart cards there are two different ways to authenticate yourself into a system, there is either contact or contactless smart card readers.

what is smart card number
how can you print on nfc cards
how to activate nfc in sbi debit card
You can try NFC Tools or the MiFare Classic Tool to emulate cards from your phone, but in my experience it's too limited. NFC tools can emulate tags but I've tried it with hotel keys and it .
token or smart card authentication|smart card identification