microsoft devices security virtual smart cards part 1 Virtual Smart Card leverages the secure storage and cryptographic capabilities of the Trusted Platform Module (TPM) to create a Virtual Smart Card in the TPM that securely stores the . A contactless card, also known as a “ tap-to-pay ” card, is a type of payment card equipped with near-field communication (NFC) technology. Contactless cards are designed to make transactions faster and more convenient by allowing .There so many factors. If the card is a high frequency card that your phone can read, and the student hostel only uses the serial number of the card (not the data stored on it), and you have a rooted Android phone and you have an app that can do that sort of thing (like NFC Card .
0 · Virtual Smart Card Overview
1 · Use Virtual Smart Cards
2 · Understanding and Evaluating Virtual Smart Cards
3 · Setting up Virtual Smart card logon using Virtual TPM for
4 · Setting up Virtual Smart card logon using Virtual TPM for
5 · Setting up TPM protected certificates using a Microsoft Certificate
6 · Provide strong Windows authentication using virtual smart cards
7 · Provide strong Windows authentication using virtual smart
8 · Microsoft Devices Security, Virtual Smart Cards Part 1:
9 · Download Understanding and Evaluating Virtual Smart Cards
10 · About the security of Virtual Smart Cards
It depends on the particular key fob system in use. Cheaper ones just use an ID number in each tag and are easy to copy. Secure ones use a challenge-response mechanism, like contactless .The problems seems to be that it's not possible to emulate/modify the sector 0, .
Virtual Smart Card Overview
Virtual smart cards are functionally similar to physical smart cards, appearing in Windows as smart cards that are always-inserted. Virtual smart cards can be used for . Customers using virtual smart cards are encouraged to move to Windows Hello for Business or FIDO2. For new Windows installations, we recommend Windows Hello for .Virtual Smart Card leverages the secure storage and cryptographic capabilities of the Trusted Platform Module (TPM) to create a Virtual Smart Card in the TPM that securely stores the .
Virtual smart cards can be used in domain-joined Windows 10 devices equipped with a TPM (version 1.2 or version 2.0). In addition, they require an accessible PKI .
Use Virtual Smart Cards
Understanding and Evaluating Virtual Smart Cards
Enroll for the certificate on the Virtual Smart Card Certificate on Virtual Machine. 1. In certmgr.msc , right click Certificates, click All Tasks then Request New Certificate. 2. On the . Virtual smart cards that utilize a TPM provide the three main security principles of traditional smart cards: nonexportability, isolated cryptography, and anti-hammering. Virtual .This document presents an overview of TPM virtual smart cards as an option for strong authentication. It provides a means for evaluating virtual smart card use in an enterprise .
This is part one of a three part series that will include the Microsoft Platform Crypto Provider, Virtual Smart Cards, and lastly the Key Attestation feature included in Windows .
Trying to have a good overview about the security of Virtual Smart Cards relying on TPMs, I read this very short article (the only I found) covering this topic (first part): . Virtual smart cards are a technology from Microsoft that offers comparable security benefits in two-factor authentication to physical smart cards. They also offer more convenience for users and lower cost for organizations to deploy. Virtual smart cards are functionally similar to physical smart cards, appearing in Windows as smart cards that are always-inserted. Virtual smart cards can be used for authentication to external resources, protection of data by .
Customers using virtual smart cards are encouraged to move to Windows Hello for Business or FIDO2. For new Windows installations, we recommend Windows Hello for Business or FIDO2 security keys. Learn about the requirements for .Virtual Smart Card leverages the secure storage and cryptographic capabilities of the Trusted Platform Module (TPM) to create a Virtual Smart Card in the TPM that securely stores the private key of the Smart Card Logon certificate to enable login via Virtual Smart Card.
how to get rfid tags
Virtual smart cards can be used in domain-joined Windows 10 devices equipped with a TPM (version 1.2 or version 2.0). In addition, they require an accessible PKI infrastructure in the environment, such as Microsoft Certificate Services. The basic process of using virtual smart cards involves three steps:
Enroll for the certificate on the Virtual Smart Card Certificate on Virtual Machine. 1. In certmgr.msc , right click Certificates, click All Tasks then Request New Certificate. 2. On the certificate enrollment select the new template you created earlier. 3. Virtual smart cards that utilize a TPM provide the three main security principles of traditional smart cards: nonexportability, isolated cryptography, and anti-hammering. Virtual smart cards are less expensive to implement and more convenient for users.This document presents an overview of TPM virtual smart cards as an option for strong authentication. It provides a means for evaluating virtual smart card use in an enterprise deployment, in addition to providing information necessary for . This is part one of a three part series that will include the Microsoft Platform Crypto Provider, Virtual Smart Cards, and lastly the Key Attestation feature included in Windows Server 2012 R2 and Windows 8.1. So getting on to part 1: Microsoft Platform Crypto Provider.
Trying to have a good overview about the security of Virtual Smart Cards relying on TPMs, I read this very short article (the only I found) covering this topic (first part): https://docs.microsoft.com/en-us/windows/security/identity-protection/virtual-smart-cards/virtual-smart-card-evaluate-security. Virtual smart cards are a technology from Microsoft that offers comparable security benefits in two-factor authentication to physical smart cards. They also offer more convenience for users and lower cost for organizations to deploy.
Virtual smart cards are functionally similar to physical smart cards, appearing in Windows as smart cards that are always-inserted. Virtual smart cards can be used for authentication to external resources, protection of data by . Customers using virtual smart cards are encouraged to move to Windows Hello for Business or FIDO2. For new Windows installations, we recommend Windows Hello for Business or FIDO2 security keys. Learn about the requirements for .Virtual Smart Card leverages the secure storage and cryptographic capabilities of the Trusted Platform Module (TPM) to create a Virtual Smart Card in the TPM that securely stores the private key of the Smart Card Logon certificate to enable login via Virtual Smart Card.
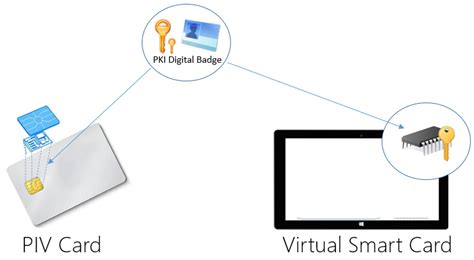
Virtual smart cards can be used in domain-joined Windows 10 devices equipped with a TPM (version 1.2 or version 2.0). In addition, they require an accessible PKI infrastructure in the environment, such as Microsoft Certificate Services. The basic process of using virtual smart cards involves three steps:
Enroll for the certificate on the Virtual Smart Card Certificate on Virtual Machine. 1. In certmgr.msc , right click Certificates, click All Tasks then Request New Certificate. 2. On the certificate enrollment select the new template you created earlier. 3.
Virtual smart cards that utilize a TPM provide the three main security principles of traditional smart cards: nonexportability, isolated cryptography, and anti-hammering. Virtual smart cards are less expensive to implement and more convenient for users.This document presents an overview of TPM virtual smart cards as an option for strong authentication. It provides a means for evaluating virtual smart card use in an enterprise deployment, in addition to providing information necessary for .
This is part one of a three part series that will include the Microsoft Platform Crypto Provider, Virtual Smart Cards, and lastly the Key Attestation feature included in Windows Server 2012 R2 and Windows 8.1. So getting on to part 1: Microsoft Platform Crypto Provider.
Setting up Virtual Smart card logon using Virtual TPM for
NFC tools has an emulate option in beta. Never tried it but if you are in the write section click on more options. . Reply reply More replies. lokogan28 • Most .
microsoft devices security virtual smart cards part 1|Download Understanding and Evaluating Virtual Smart Cards